Please note instructions updated to include perfc.dat and perfc.dll files.
The advise on the files needed to prevent the encryption now included creating perfc.dat and perfc.dll files in the Windows directory in addition to the one without an extension.
Please note: this does not prevent the spread of NotPetya, at this time until the software is updated to prevent this from working, this just stops it encrypting your computer.
Following today’s(27th June 2017) manor cyber-attack outbreak for the NotPetya/GoldenEye bleepingcomputer have published an article on Vaccine, not Killswitch, Found for Petya (NotPetya) Ransomware Outbreak
They have supplied a bat script or instructions to apply this manually but if you want to apply it so the computers will receive it without a reboot you could use Group Policy Preferences.
- On a file share, the targeted computers have access to (e.g. read access by domain computers and domain controllers)
- Create a directory
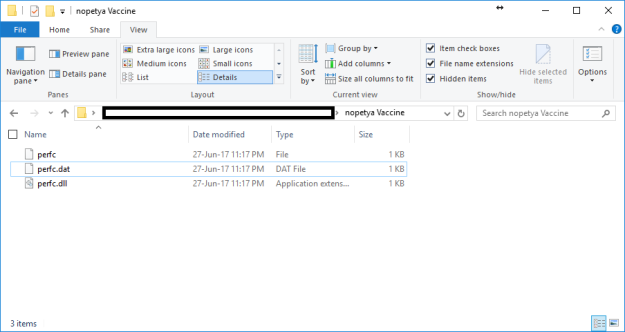
- Create a file named perfc (no file extension)
- Add some content to the file explaining what its for (example in the sctript linked above is “This is a NotPetya/Petya/Petna/SortaPetya Vaccination file. Do not remove as it protects you from being encrypted by Petya.”)
- Set the file to read only
- copy this file twice
- rename one to be perfc.dat
- rename the other to be perfc.dll
- Check all three files are readonly
- you should now have three files in that directory perfc, perfc.dat and perfc.dll
- Create a new group policy or edit an existing one targeted to all the computers you want to deploy the vaccine file to
- Edit the group policy
- Under Computer Configuration -> Preferences -> Windows Settings – Files
- Right click and select new -> file
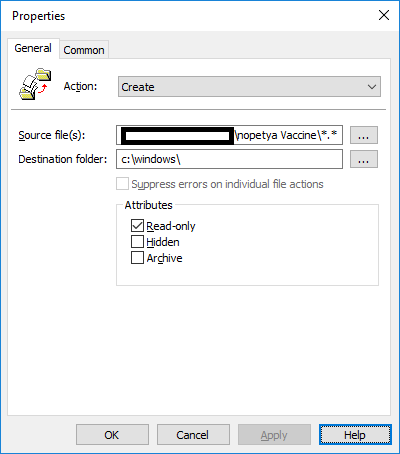
- In the source file location enter the path to the directory you created earlier and append \*.* to the end of the path – e.g. \\server\share\nopetya Vaccine\*.*
- In the destination file enter c:\windows\
- Select Read-only
- Action should be create (note this will only create the files if they does not already exist in the destination) this is preferred as you would not want the files on the server if compromised to be copied again to the clients. Please note – any file in this directory will be copied to the c:\windows\ directory. If your not happy with this, you could create three ‘new -> file’ entries in the GPO, each explicitly naming the files you want to copy
- Click OK
- run GPupdate /force on some computers to check
- the file “c:\Windows\perfc” is created and is read only
- the file “c:\Windows\perfc.dll” is created and is read only
- the file “c:\Windows\perfc.dat” is created and is read only
I accept no liability following this instructions of those found on third party websites I have linked to.
